Social Engineering.
Social engineering is one of the biggest threats to businesses and organisations of all sizes, from start-ups to international corporations.
Don't risk it
Social engineering, the art of manipulating individuals to reveal confidential information, grant unauthorised access, or perform certain actions, is one of the most significant threats to your cybersecurity. Cyber criminals are increasingly turning to psychological tactics to exploit human vulnerabilities. Understanding and defending against social engineering attacks is now vital in safeguarding individuals and organisations from cyber attacks.
For those that fall prey to a social engineering attack, the consequences can be severe, with damages possibly costing millions and a brand’s reputation can be destroyed.
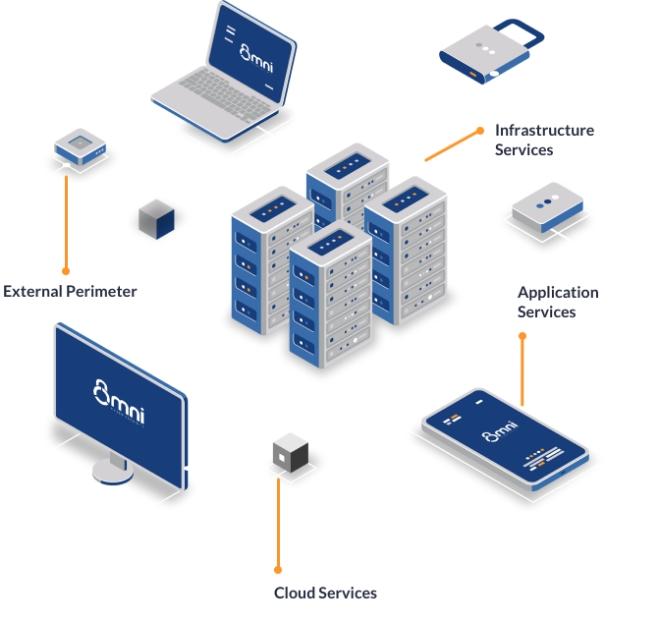
Social Engineering Summary
-

What Is Social Engineering?
Social engineering is a technique used by cybercriminals where psychological manipulation is used to get members of your workforce to click on links and attachments, or divulge sensitive information. In short, social engineering sees your employees coerced into revealing confidential information or coerced into performing adverse actions.
-

What To Look Out For
Cybercriminals are adept at creating web pages and emails that look legitimate, in their effort to get people to click on links, open attachments, or share personal or company data. This makes it more difficult to know who and what to trust.
-

How To Prevent Social Engineering
Social engineering testing is the first defence against fraudsters using these tactics. A test will assess your company’s systems and personnel, for their ability to detect and protect against these types of malicious attacks. Testing methods are designed to mirror the techniques used by criminals to highlight weaknesses. The results can be used to improve your workforce’s awareness of cybersecurity.
Talk to one of our cybersecurity consultants
The best defence
The best defences against social engineering include:
- Educating your employees not to open emails from untrusted sources.
- Educating your employees not to click on links or download attachments.
- Employing a cyber security company to run social engineering testing.
- Choosing a cyber security company that can run white-box and black-box simulations.
- Choosing a cyber security company that uses CREST-accredited ethical hackers, like OmniCyber Security.

