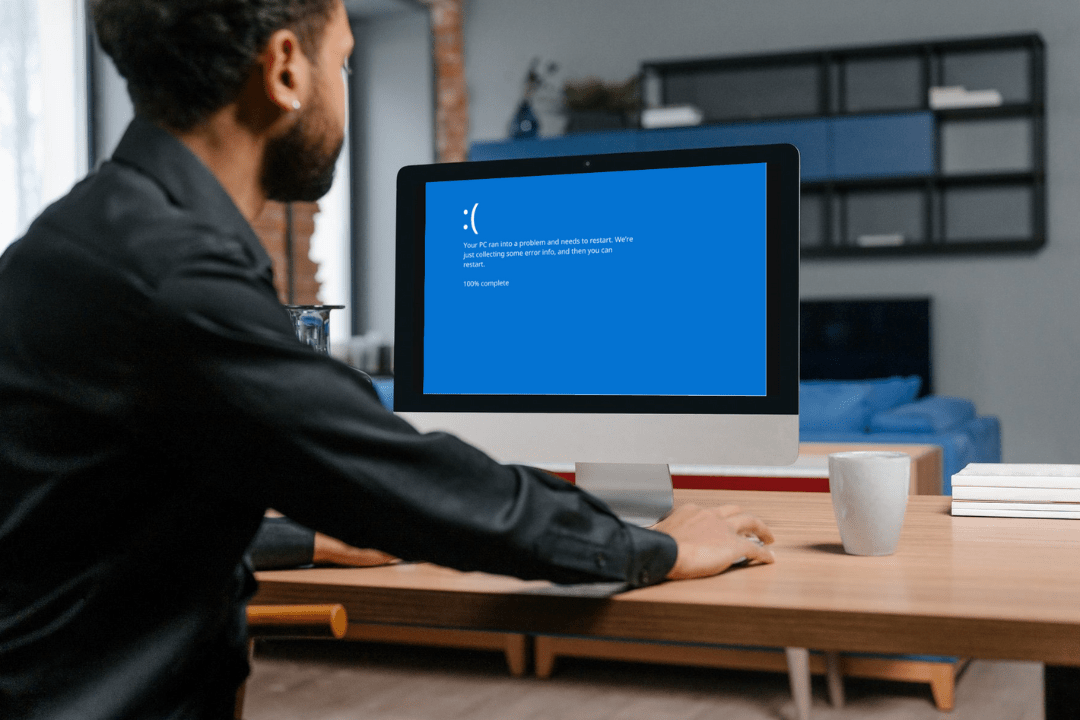
The Biggest IT Outage In History: What Happened?
Move over Y2K, there’s a new legendary outage in town. A broken software update has crashed Windows devices around the world, bringing airports, TV channels,

Move over Y2K, there’s a new legendary outage in town. A broken software update has crashed Windows devices around the world, bringing airports, TV channels,
Your organisation’s security extends beyond its own walls. Every organisation has suppliers. Whether they deliver products, systems, customers or services, the modern landscape of business

ISO 27001 is the internationally recognised standard for information security management systems (ISMS). It provides a robust framework that helps organisations manage their information

The Payment Card Industry Data Security Standard (PCI DSS) is a security standard designed to ensure that all companies that accept, process, store, or transmit

Cyber security is a top priority for businesses in all industries. As cyber threats continue to evolve, it’s crucial to protect your organisation. One way

The goal of penetration testing, often referred to as pen testing, is to validate the effectiveness of your current security controls. It’s a critical component

It’s often said that your employees are the biggest threats to your cyber security. This usually refers to a lack of education leading to employees

ISO 27001 is an internationally recognised standard for information security management systems (ISMS). It provides a systematic approach for organisations to manage and protect their

If you process card payments, you must be PCI DSS compliant. PCI DSS (Payment Card Industry Data Security Standard) is a program created by the
A penetration test, also known as a pen test, is a simulated cyber attack on an IT system, performed by a professional without malicious intent.
With vast amounts of sensitive information, including employee details, customer records, financial data, and intellectual property, stored and processed daily, modern organisations are increasingly vulnerable
Half of businesses have suffered a cyber security breach in the UK in the last year, according to the government’s annual Cyber Security Breaches survey.

In short, if your business accepts card payments, it must be PCI DSS compliant. The Payment Card Industry Data Security Standards (PCI DSS) apply to

Cyber Essentials is a UK government-backed certification standard that helps you create an essential security baseline to protect your business from everyday cyber threats. A

Penetration testing, also known as pen testing or ethical hacking, is a vital part of a solid cyber security strategy. It involves a simulated cyber